Using Wireshark To Analyze The GRPC/ProtoBuf Messages
First run a gRPC server:
Build the project firstly:
$ mvn install
Then run the gRPC server:
$ mvn exec:java -Dexec.mainClass="greeting.server.GreetingServer"
If everything goes fine the server is started:
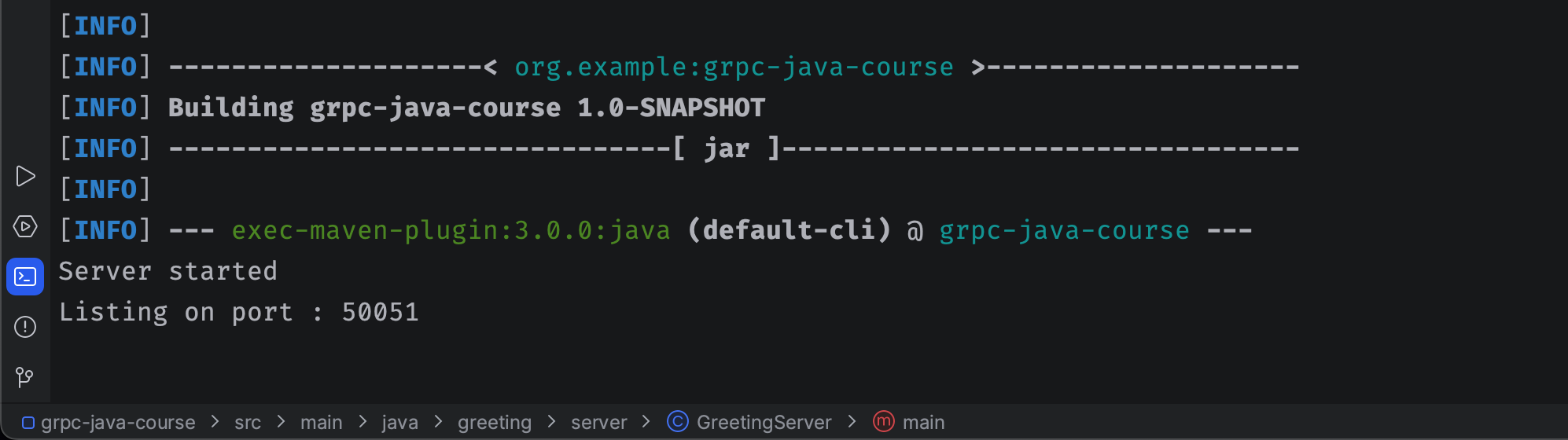
The above example project opens a gRPC service at port 50051, then we can open Wireshark and start to capture packets at lo0:
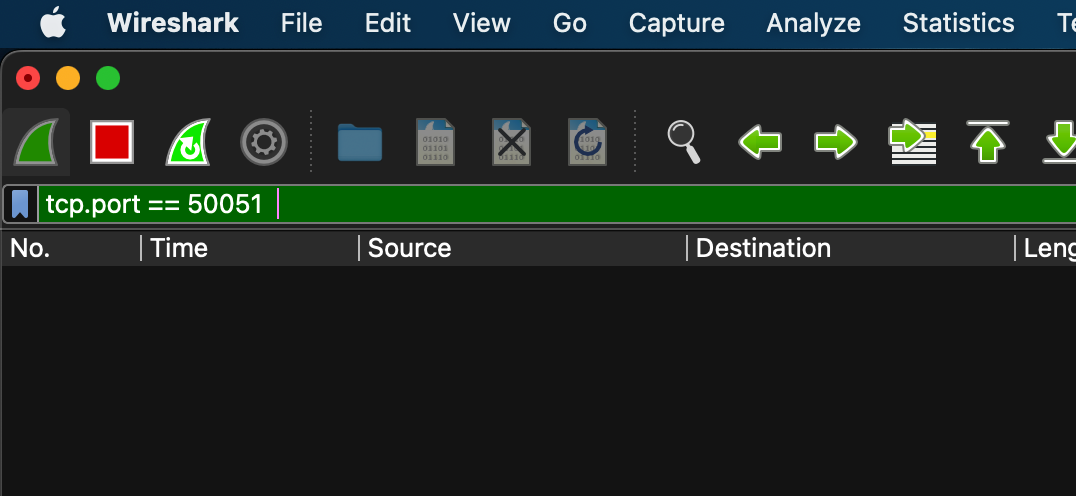
There are heavy traffics at lo0, and we just need to check the packets at port 50051, so we can user the filter to display the packets at port 50051 only:
And then we can use the tool grpcurl to do the request to the service:
➤ grpcurl --plaintext -d '{"first_name": "foo"}' localhost:50051 greeting.GreetingService/greet
{
"result": "Hello : foo"
}
And now we can see Wireshark has captured the packets between the communication:
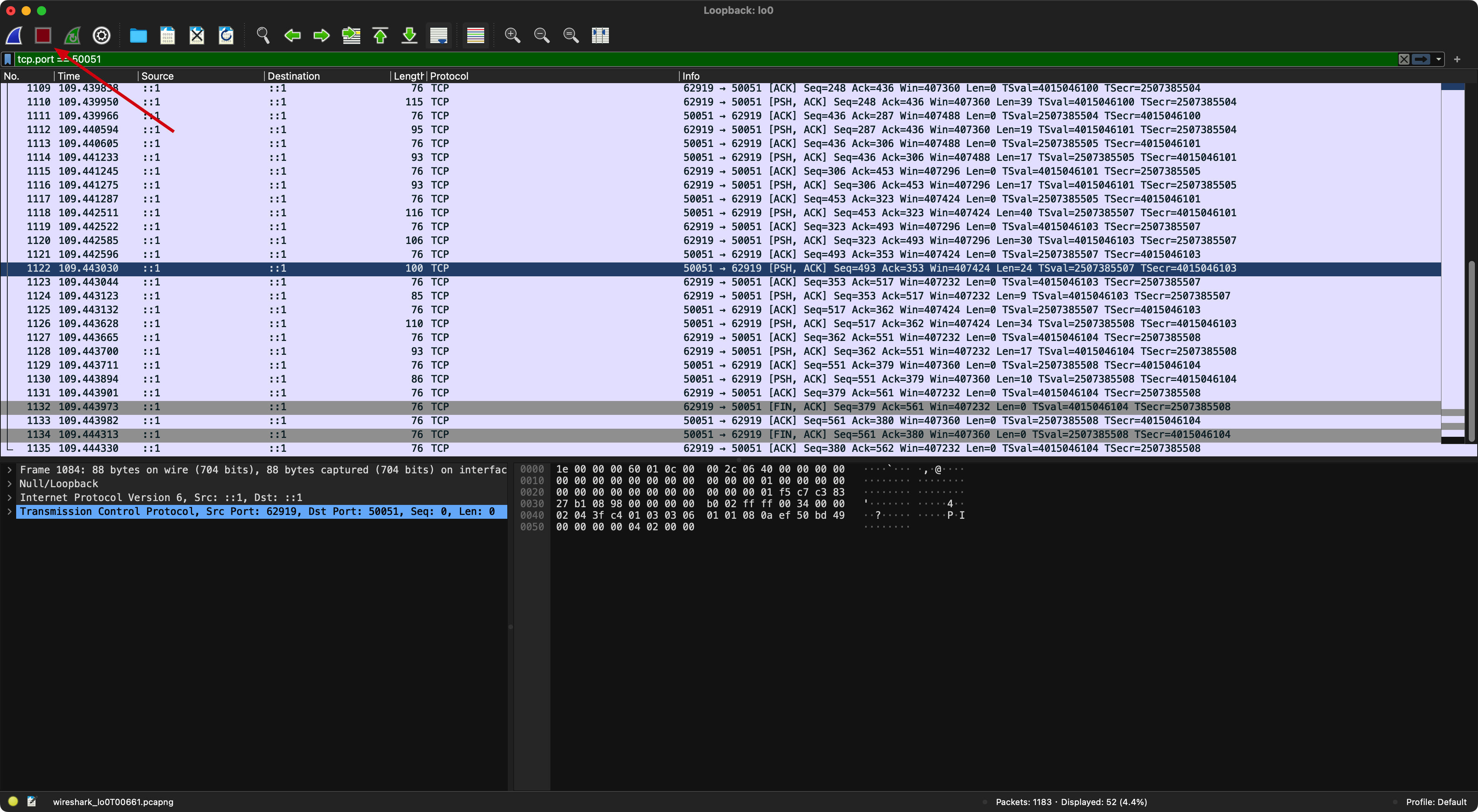
From the above screenshot we can see the packets are captured and they are interpreted as TCP packets. We can right click one of the packets and select Decode As...:
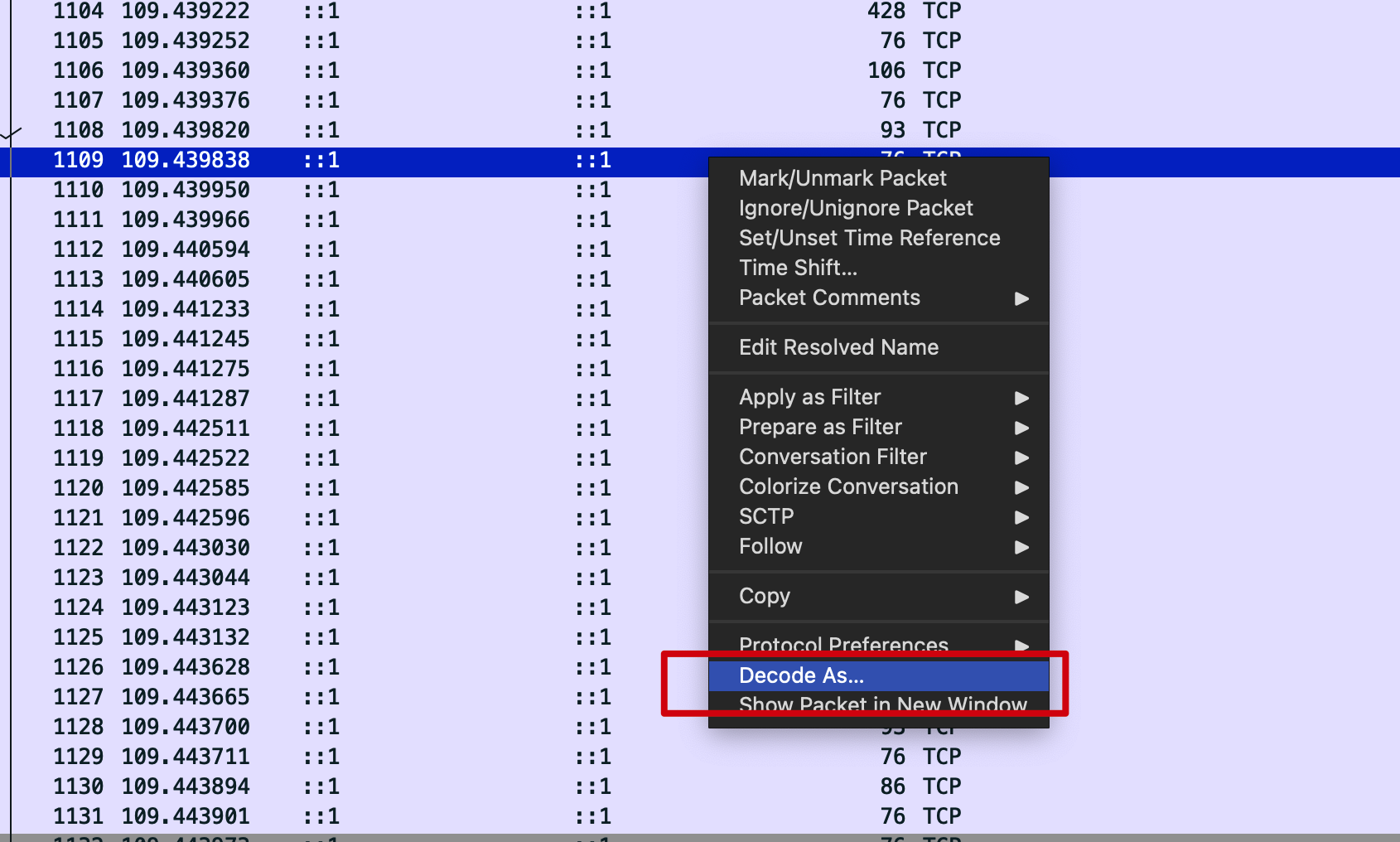
And then ask the Wireshark to decode the packets at port 50051 as HTTP2 and click OK:
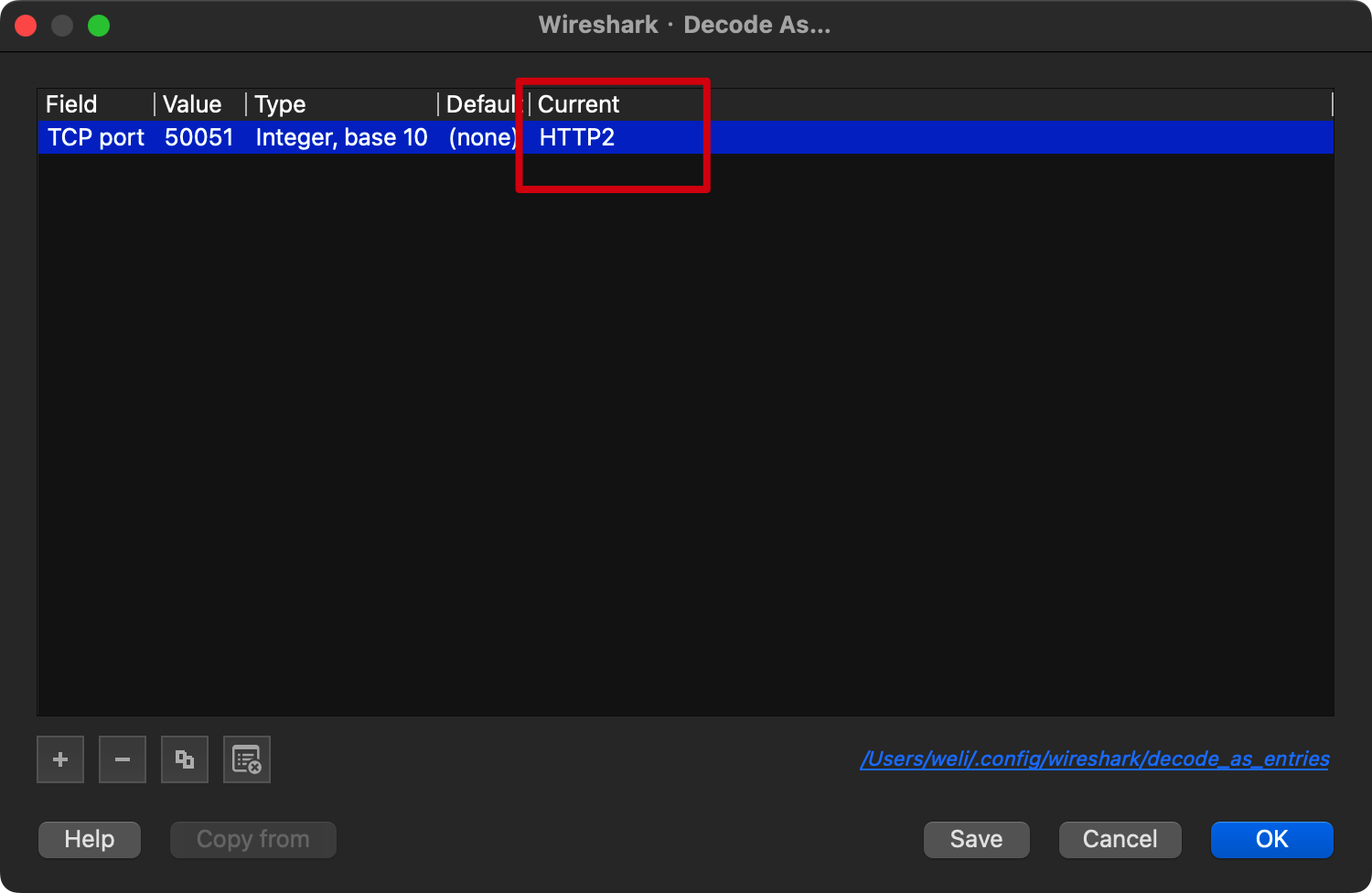
Now the HTTP2 packets can be interpreted, and the GRPC communication can also be recognized:
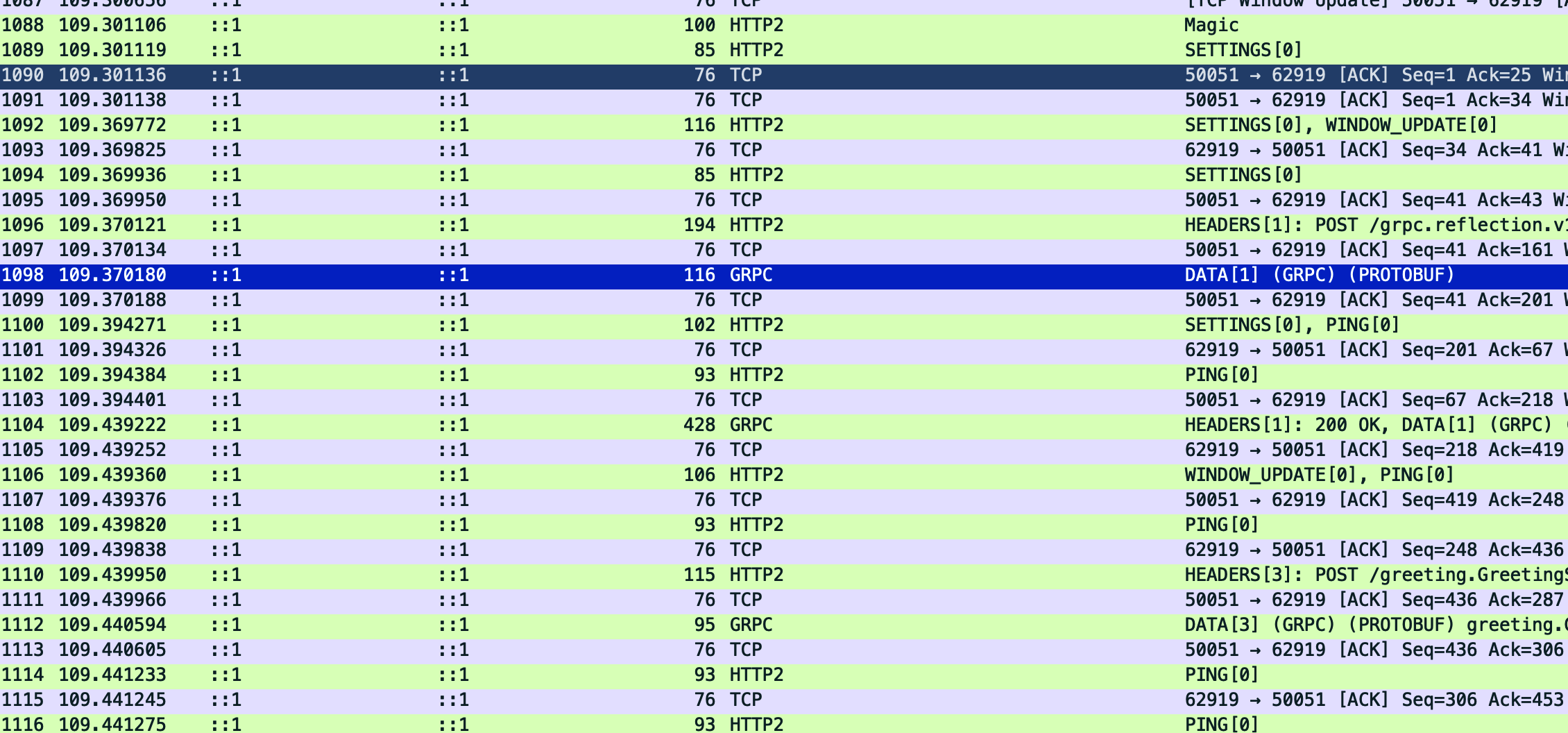
To let the Wireshark understanding the detail message format in the GRPC communication, we can select one of the GRPC messages and right click it and select Open Protocol Buffes preferences... as shown in below:
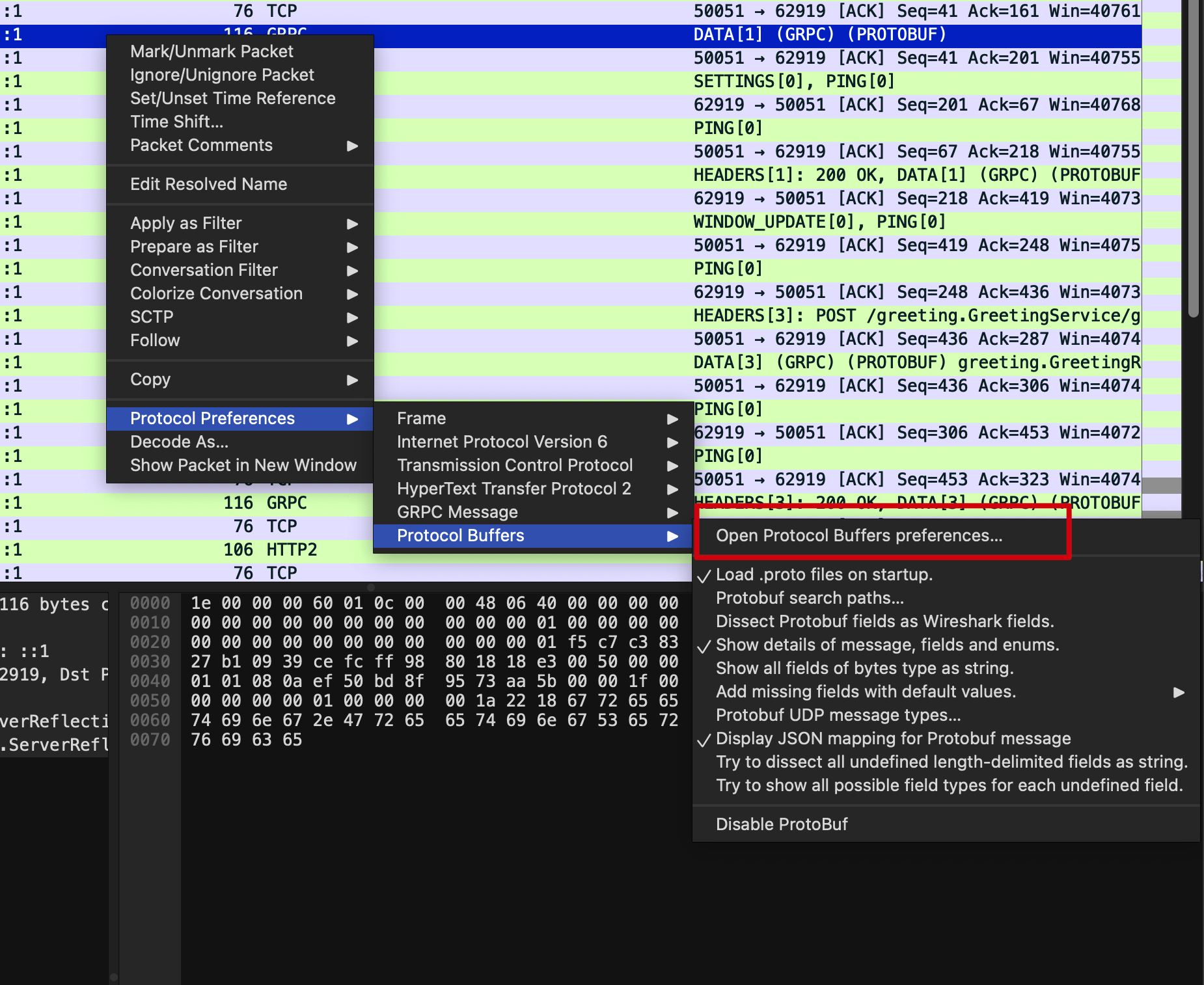
And then select the ProtoBuf config tab and edit the Protobuf search paths to select the .proto file used in the communication:
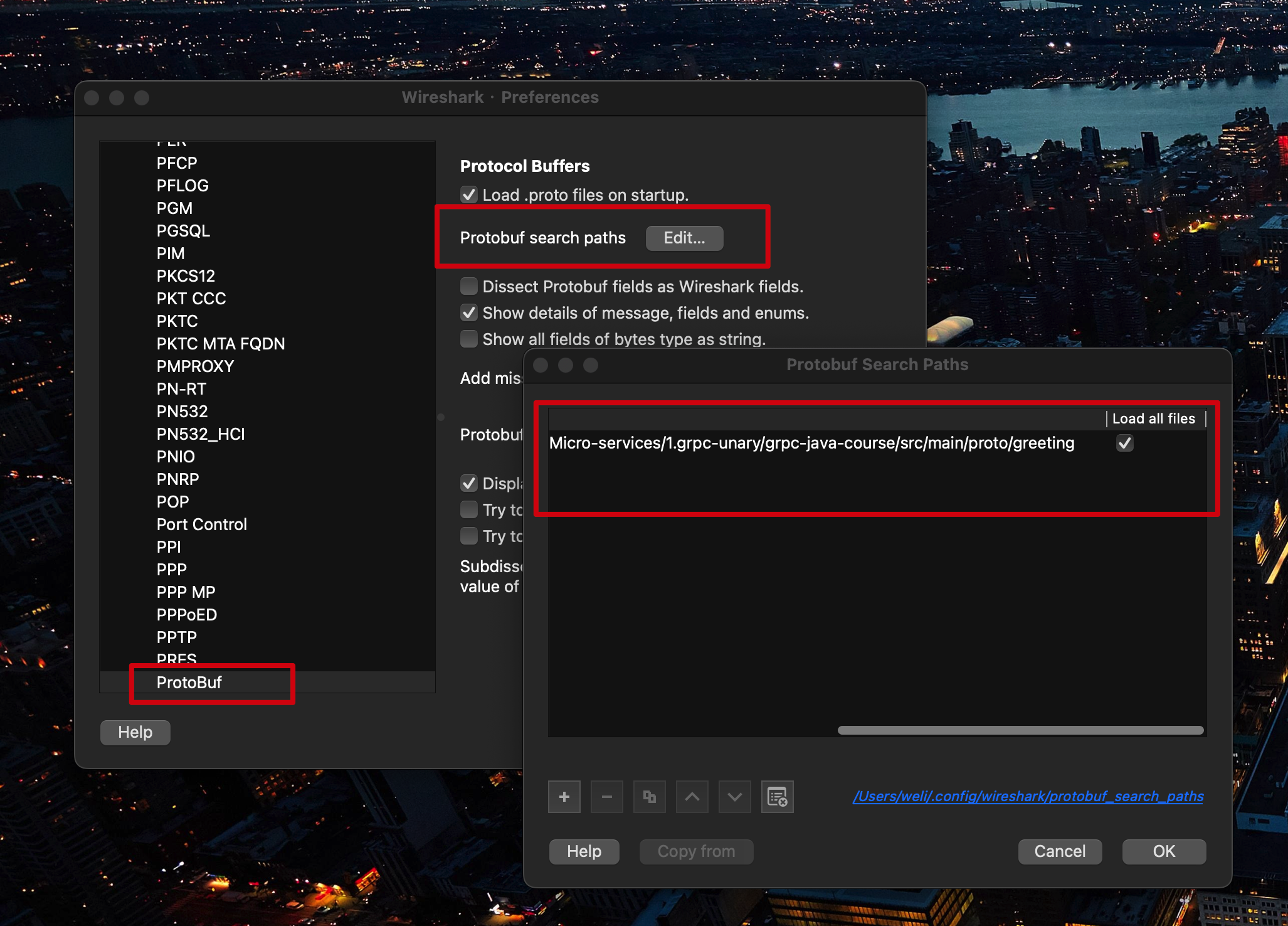
As the screenshot above, we have selected the .proto file path used in the example project. The .proto file is defined like this:
syntax = "proto3";
package greeting;
option java_package = "com.proto.greeting";
option java_multiple_files = true;
message GreetingRequest {
string first_name = 1;
}
message GreetingResponse {
string result = 1;
}
service GreetingService {
rpc greet(GreetingRequest) returns (GreetingResponse);
}
In addition, I have enabled these two options in the config:
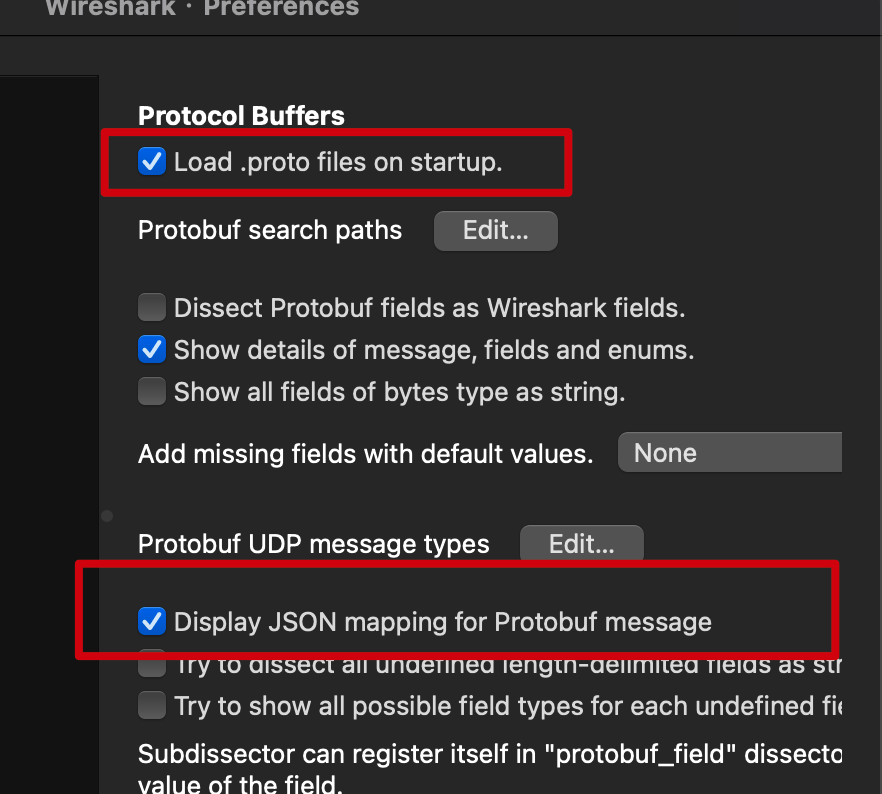
After clicking OK to finish the setting, the packets capture window are refreshed, and the data structure can now be recognized by Wireshark. We can double click one of the GRPC packet:
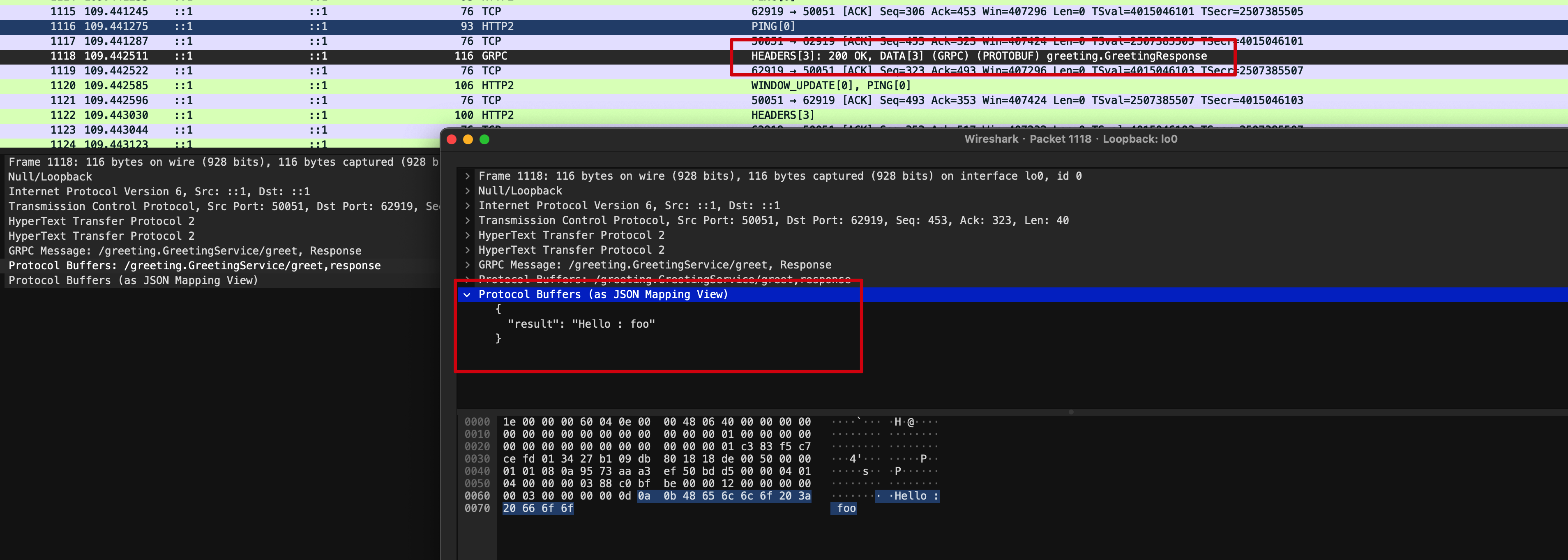
As the screenshot shown above, we can see the message structure can be interpreted.